Also called De-militarized Zone (DMZ)
Type of network that is used to be separate the Internet from the organizations network
Untrusted users outside an organizations LAN can access services within the DMZ
Acts as a security barrier between external untrusted networks and internal trusted networks using a protected host with security measures like a packet-filtering firewall
Two types of common configuration: Leg Configuration & Back-to-Back Configuration
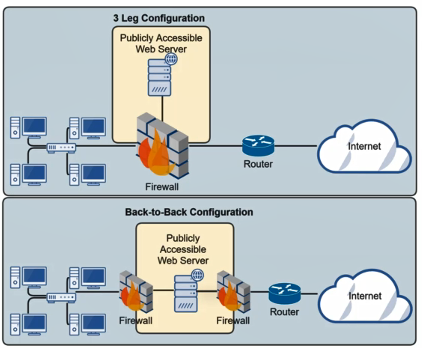
Devices placed in the Screened Subnet as called Dual-homed Hosts
These devices have two network interfaces one that is connect to the internet and the other that is connected to the internal network
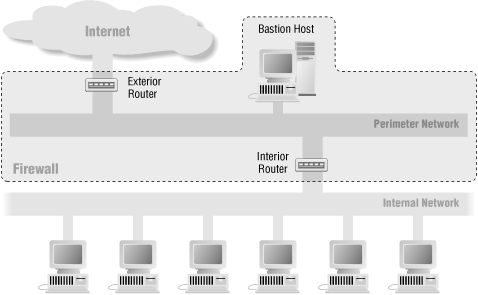
Screened Subnet Architectures (Building Internet Firewalls, 2nd Edition)